It’s cliché by now:
Your users are your best cyber defenders.
I hear that and sometimes I feel it’s getting old, but it’s so very true. In this article, let’s take a look at Business Email Compromises (BECs), and how we can empower our people to protect the business from them.
I’m selecting BEC as an example for this article so I can be specific, but remember that we should be empowering our users to protect us from a variety of user-borne attacks.
What is a BEC?
Of course, we need to define our attack here. A Business Email Compromise can come in a couple of flavors:
-
Compromised Credentials. This is the worst kind. I’ve popped the CEO’s credentials who doesn’t have MFA, or maybe I stole their session token, and I’m sending email from their valid account. I did this with a phishing attack or something of the like.
-
Impersonation. This is the most common type of attack. Let’s say our CEO is Jane Smith. If I want to impersonate them, I head on over to Google and I create an account janesmith123871(@)gmail.com with “Jane Smith” as the display name. This is super easy to do as Google, Microsoft, Yahoo and others don’t (and really can’t reasonably) check this all the time.
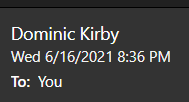
In this article, I’m going to look at the impersonation method. This relies on one very common weakness: people don’t often observe the email address when they are reading an email, just the display name.
Example email, only showing a display name.
In fact, as you can see above, we often don’t even see the address in our email client. This is what I, the attacker, want to take advantage of. I’m going to send an email from “Jane Smith” (the CEO) asking that you do something advantageous to me. This often looks like “Our vendor XYZ is asking us to wire the payment to a new account” with some account details.
You, the innocent finance recipient, see that this is from your CEO, prioritize it, and send me the money. Only, I’m not vendor XYZ. I’m a bad guy. And I just received money that you authorized the bank to send me (good luck getting it back, most of the time).
Okay, that’s the attack. Simple yet elegant, and wildly effective. Let’s stop it.
Not Today, Threat Actor
How can we stop this from happening? Well, here’s the catch. The email doesn’t look particularly scammy (no weird links, valid SPF, DKIM, DMARC, etc.), so a lot of email security filters are going to interrogate it and pass it on through. We have to get more creative.
Technology
There’s some tools in this space such as Ironscales and Defender for Office 365 that do an excellent job helping with BEC. The former can present an alert message that says something like “We know Jane Smith, but this isn’t Jane Smith’s normal address.” Easy enough, that should trigger some second thought.
The ladder, Defender for 365 from Microsoft, can have Phishing Protection enabled for key users, filtering out messages from non-work addresses. Both of these are powerful tools, but they aren’t perfect.
People
People are the lifeblood of any company. They do the amazing things that make your company function. They are also, by default, the weakest link in your security strategy. We have to teach them what they’re up against. We do this through a number of training programs, testing programs, and perhaps even a lunch and learn on phishing and BECs. Stats all over the place show that this can be very effective at preventing these attacks. But there’s a second piece to this puzzle I often see people miss, empowerment.
Simply training our users is not enough. We have to give them the power they need to stop an attack.
Once we teach them the threats that face them, we need to tell them that it’s okay to stop, analyze, and refuse to do something that seems out of the norm before validating it. This comes down to process (I’ll touch on that in a moment). But, it also comes down to telling the team that just because the CEO said it doesn’t mean do it right away. Take the time to analyze what’s being asked of you, see if it’s normal, and intervene if it isn’t.
Everyone on the team must feel safe stopping, analyzing, and saying no (or wait) while they validate an ask. They must feel safe doing so without replying to “Jane Smith,” and they must know there will not be negative repercussions for taking action to protect your business.
Once they know they’re empowered to be a defender, they wont’ be nervous about doing it!
Process
This is the final piece to the BEC defense puzzle. For sensitive actions (such as dipping into the company money), there should be well defined processes that are followed every single time. Any deviation from process should result in an immediate stop and refusal to move forward.
It’s easier said that done. The human condition is to help. But, if we have a procedure in place that the right people know and understand, it makes it much easier to identify “wrong.”
Here’s an example process that I’ve implemented for a customer in the past (for invoice payments specifically):
-
The person who needs an invoice paid submits a request through a Microsoft Form
-
The uploaded invoice is saved to SharePoint, and a SharePoint list item is created to rack progress
-
Power Automate sends a request to the CFO with the details and a link to the invoice
-
The CFO validates this request and approves (or denies) it
-
The request goes to the controller, who triple checks everything (the controller also has the payment procedures for each vendor, and can validate changes)
-
If everything looks good, the controller handles the payment and bookkeeping.
-
If at any point something deviates or doesn’t look right, any process stakeholder can stop the process. This could mean calling the requester at a known number to double check the request, calling the vendor about a “change in process” or simply denying things altogether.
-
Once this process was implemented, people who receive invoices were briefed. In that business, it doesn’t matter if the CEO sends an email. If it’s not submitted properly, the payment request never finishes and no check is written (or money wired). Anecdotal: this process was mobile friendly so the stakeholders could conveniently submit requests as needed*.***
As a part of this request, the requester and approvers had to authenticate with their corporate account (with MFA and conditional access, the works), so the requests were authenticated as well.
In Summary
There’s three key points I’m aiming to drive here:
-
People really are your best defenders. Educate them, and give them power to be that defender.
-
The simplest of attacks (signing up for Gmail) have the easiest time sneaking past some of the best technology on the market.
-
Processes make it easy for your people to make smart cyber defense decisions on the fly, even under the pressure of “a request from the CEO.”
As a security practitioner, you should always be looking for creative ways to empower everyone to be a cyber defender.
There are links in this article to Pax8's website. These are not compensatory and I'm simply referencing a product I support.