Raw Thoughts
Communicating Outages Out of Band
Over the weekend (on 3/1 to be exact), there was a significant outage at Microsoft impacting primarily Exchange Online but also some other services. Even though this outage was relatively short, many MSPs reported receiving lots of emergency calls, texts, tickets,...
Let’s Stop Device Code Phishing!
Device code phishing is a real threat that often goes unmitigated. Microsoft's recent warning that threat actor Storm-2372 is actively executing a device-code phishing campaign drives that home. If you want to learn more about device-code phishing, check out the...
2025 in Cybersecurity (and a Look Back at 2024)
It's hard to believe that we're closing in on the end of 2024. For me at least, it has been one of those years where being busy keeps the time moving! It's also been an active year in cybersecurity so, in the spirit of turning the page, let's have a look back at 2024...
Is Your Documentation Version Controlled?
One of the only constants in technology is change. Technology advances, we implement new stuff. Or, some sort of upgrade or new version changes the way we do things. At the same time, successful technology and cybersecurity management is hinged on effective...
Ready. Set. (Entra) Passkey!
Now that Passkeys are generally available, we can start thinking of strategies to implement phishing resistant authentication in our environments! Microsoft has provided a lot of guidance on rolling out Passkeys in general. In this article, I'll talk through some...
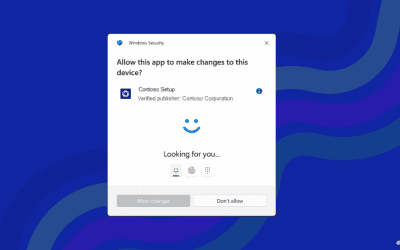
Windows 11 Getting Just in Time Administrator Protection
In another cool Ignite share, Microsoft announced Administrator protection on Windows 11. This feature aims to protect users from malicious code or intent by creating "just in time" administrator privileges for local admins. This is an awesome, and overdue feature,...
Passkeys in Authenticator are Generally Available!
Awhile back, Microsoft released a preview of soft Passkeys in Microsoft Authenticator. At its core, this feature delivers a cross-device authentication FIDO credential, encapsulated securely within the Microsoft Authenticator app, bound to the device on which it's...
Mandatory MFA is Finally Upon Us
We're a little over a month out from Microsoft's upcoming MFA mandate. On October 5th, 2024, the Entra Admin Center, Intune Admin Center, and Azure portal will finally mandate multifactor authentication. This means that, regardless of your tenant settings, you will be...
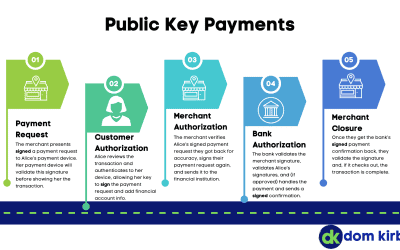
Can Payments take a Page from the FIDO book?
Payment card fraud is as old as payment cards themselves. First, we used embossed cards and phone calls in the clear to process payments. Then, we had to trust service staff to take our cards away from us to process them. The majority of them were just doing their...