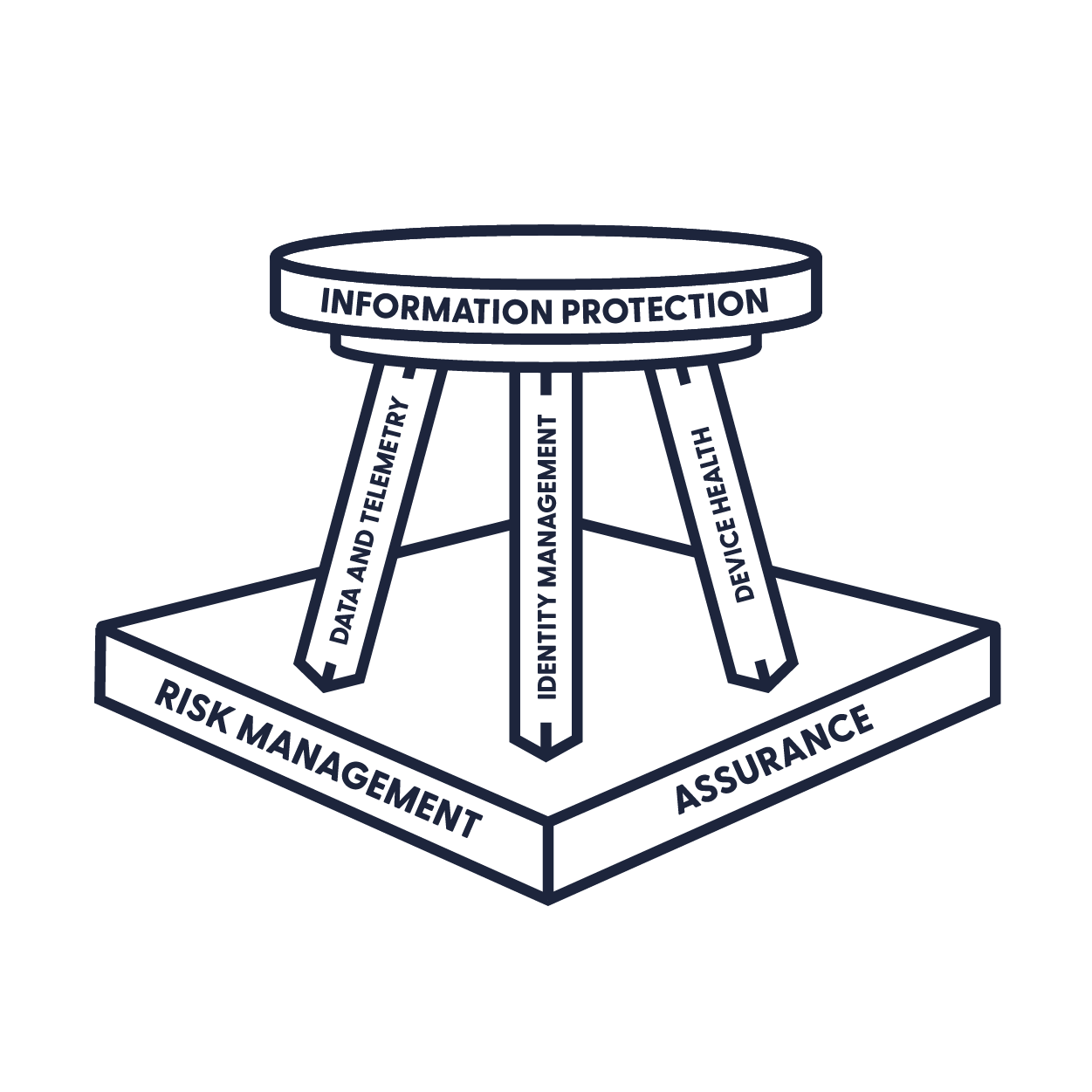
When I talk about security in the Modern Workplace, I very often use the “three-legged stool”
I’m a fan of this model because it’s easy to explain, and the different legs in the stool can easily be attached to pretty much any framework. Most importantly, the stool has three legs. If you neglect one, it’ll break and the whole thing will come falling down. That would suck, right? In this article, I would to talk about Device Health, and some common misconceptions about how we can manage it in Modern, cloud-first, and BYOD environments.
What is Device Health?
Like with everything, context helps. So let’s talk through what Device Health means to me. Really, it’s simple. When inching towards zero-trust, or even establishing good security baselines, we need to know the who what when and where related to accessing our data. Naturally, we need to make sure the people accessing data are supposed to do so. Knowing when is also a no-brainer, any forensic investigation is useless without time. Where is becoming more and more important as time goes on. We want to be able to spot things like impossible logon, or trends that just don’t match up (I could do a whole writeup on where, stay tuned perhaps). That brings us to what. We need to understand what devices are being used to access our data, and we want to know that they’re safe.
If I connect to SharePoint and head to the company trade secrets (even with MFA et al.), you’re screwed if my machines has already been compromised. Device-level access is an incredibly powerful tool because we’ve spent so much time placing inherent trust in authentication without factoring in the device. Problem is, if I’m on the device already and you authenticate, I have everything I need to get your data.
A little Metasploit or Cobalt Strike action, and I can access anything your machine can. The key to device health is making sure the device is configured to security levels we’ve deemed acceptable for our organization. Plain and simple.
As an aside, MDM and MAM also help us protect from insider threats. Being able to remove work data after a termination is an essential capability.
Sidenote: I’m going to focus on Microsoft technology in this writeup. However, there are plenty of tools you can add to your toolbox to achieve this goal.
Enter: Mobile Device Management (MDM) and Mobile Application Management (MAM)
When combined in an overall security strategy, these two methodologies are incredibly powerful. The difference between the two is covered in the name: we can manage things at the device level, or at the application level. Which model we use on which device – for me – really comes down to who owns it. I don’t want full control of personal devices, ever. There’s liability, the perception of “big brothering,” and a bunch of other things I just don’t care to deal with (save for better tech like Android Enterprise Work Profiles).
Corporate Devices
Let’s start with the low hanging fruit. If your company (or customers) dishes out Windows machines, life is gonna be real easy on you! Join those machines to Azure AD (or Hybrid Join them) and enroll them into Microsoft Endpoint Manager. You’ll have almost the entirety of Group Policy (assuming you’ll let go of some of those frivolous one’s we’ve all been guilty of writing), as well as compliance policies and configuration profiles. Using Endpoint Manager, you’ll be able to set a policy that requires encryption, patching, deploys your EPP of choice, deploys key work applications, configures the desktop on behalf of the user, and pretty much anything else you want it to do.
For the time being, macOS is a little trickier but it’s REALLY coming along. Until Azure AD Join for macOS comes out, you’ll need do a little more work. You’ll setup Apple Business Manager, glue your identities to it with Azure AD, and glue Endpoint Manager to it. From there, you’ll have a comprehensive amount of control to make sure you have encryption, EPP deployed, and all those other goodies we talked about.
I’m not going to get into what should be in your policies. You need to align your standards of configuration and security with your overall security program. Whether that’s super simple “must be encrypted” all the way down to desktop wallpapers, if that’s your thing.
Protip: Deploy all the apps you can with MEM. It will make the user experience so much better. Seriously. When I swapped corporate PCs I just waited and hour and was ready to rock. Autopilot + MEM is one of the best Microsoft inventions ever.
Bring Your Own Device
This is where it gets tricky. Let me start by saying, I love BYOD. Like seriously, who really wants to carry two phones around?! Not me!! So, let’s talk through how we can protect data on BYOD devices, without asserting too much (or really any) control over the team’s personal data. This is the scenario where we talk advantage of Mobile Application Management. Instead of managing the whole device, we take advantage of supported applications and force requirements on the security features of those applications. I always build a policy that covers the “most common entry point apps” into Microsoft 365: Outlook, Teams, Office, SharePoint, OneDrive. To extend beyond that, think about “stumbled upon apps” like ToDo, Planner, etc.. Also be sure to check your third party, SSO integrated apps. The list of supported third-party apps for MAM is really growing quick.
With a MAM policy, we can set some basic principles up:
-
Users must somehow authenticate to access data. This can be done with a PIN code that’s specific to the app, and you can allow that PIN to be overridden by device auth (requiring a screen lock on the device)
-
Mandate encryption of company data. In particular, all of the Microsoft apps have self-contained encryption on board, meaning that work data is stored and encrypted within its own enclave.
-
Prevent moving company data to personal storage. This is a big one! If we protect the OneDrive app, we need to keep the data in OneDrive or at least in our approved ecosystem. We do that by blocking to ability to save files to device storage, non-company storage services, etc.
From there, we have users use approved apps (Outlook for email, etc). We can enforce that with conditional access.
In this scenario, we’ve successfully protected our work data on a personal device without taking control of the device. We’re only controlling the apps (or really the pieces of the apps) that contain work data. We can’t wipe the whole device (that’s a good thing)! But, we can securely remove the work data from their device, leaving the user’s Instagram, family photos, and other personal data unharmed. It’s really the best of both worlds!
Bonus: Once these methodologies are implemented, you’ll be able to report on them from right within Endpoint Manager. When the auditor comes knocking, asking you to prove disk encryption, you’ll be able to show it right from the Microsoft Endpoint Manager Admin Center..
If you have any questions, please let me know!