If you watch my content, you know I love me some U2F, but why?
Category: Cybersecurity
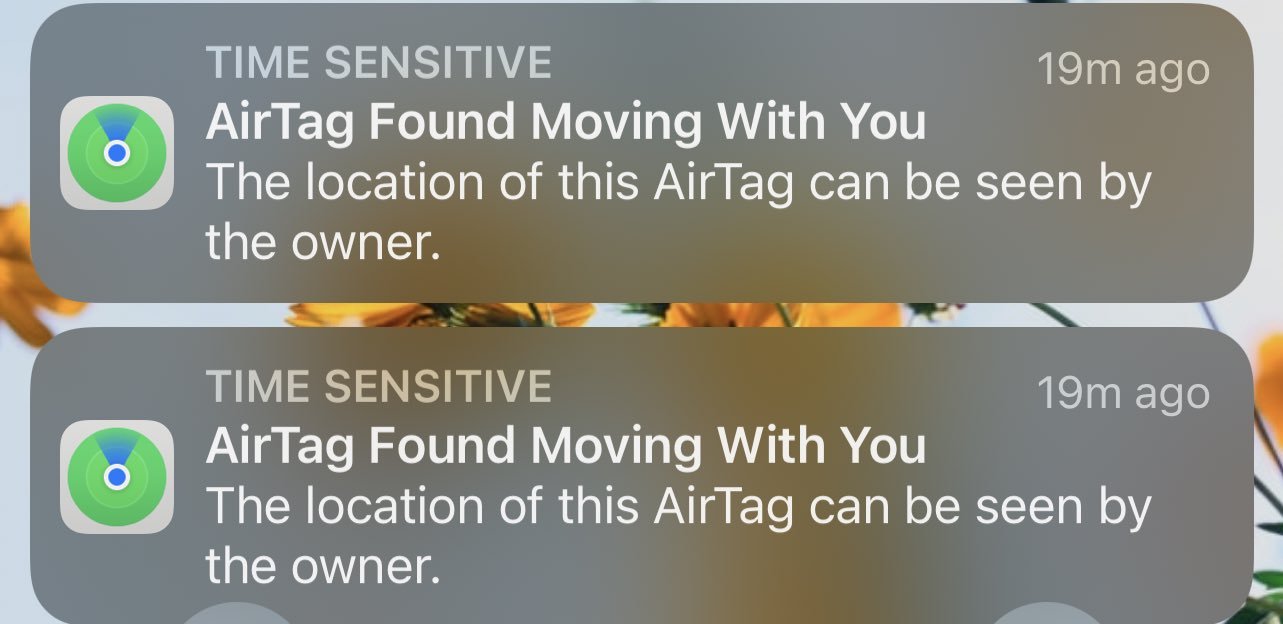
The AirTag Conundrum: Apple Needs to Fix This!
AirTags are being used to stalk folks, and it needs to be fixed!
Cybersecurity in 2022: Don’t do it alone!
It goes without saying that the cybersecurity landscape is changing... rapidly. We're seeing a huge rise in attacks like ransomware, phishing, extortion, and more. More to the point, we're seeing a huge rise in these attacks amongst the small to medium business...
Is Your “Patch Management” Doing More Harm Than Good?
Patch management is becoming a more debated topic nowadays. The proliferation of Intune's simplified patch management across Windows environments has upset some. and made others (like me) quite pleased. Let's talk...Patch Management: Circa 2014Let's talk about how we...
Modern Work Security Tip: VPN
VPNs can be a critical tool in protecting users and data when they use untrusted networks, such as public Wi-Fi.
Cyber Insurance is Getting Harder to Acquire for SMBs… Sort of
There’s been a significant amount of chatter around Cybersecurity Insurance for SMBs. Insurance carriers and underwriters are ratcheting up requirements for getting a policy, and the attestations are getting more and more intense. Of course, this makes things harder...
Is it Time to Let Go of Your RMM?
This question is quickly becoming the hottest question in the channel, especially after the Kaseya incident. In this article, I’ll illustrate a kill chain with an RMM-based attack, some thoughts on attack surface reduction, and some thoughts on ditching the RMM altogether.
Managing Device Health in the Modern Workplace: Why it Matters
The Microsoft three-legged stool model. When I talk about security in the Modern Workplace, I very often use the "three-legged stool"I'm a fan of this model because it's easy to explain, and the different legs in the stool can easily be attached to pretty much any...