Via The Record 5JAN22 - The Federal Trade Commission made an announcement on Tuesday that it may pursue legal punitive action against entities who experience a breach of consumer personal data as a result of failure to patch against Log4Shell and future ‘similar known...
cybersecurity
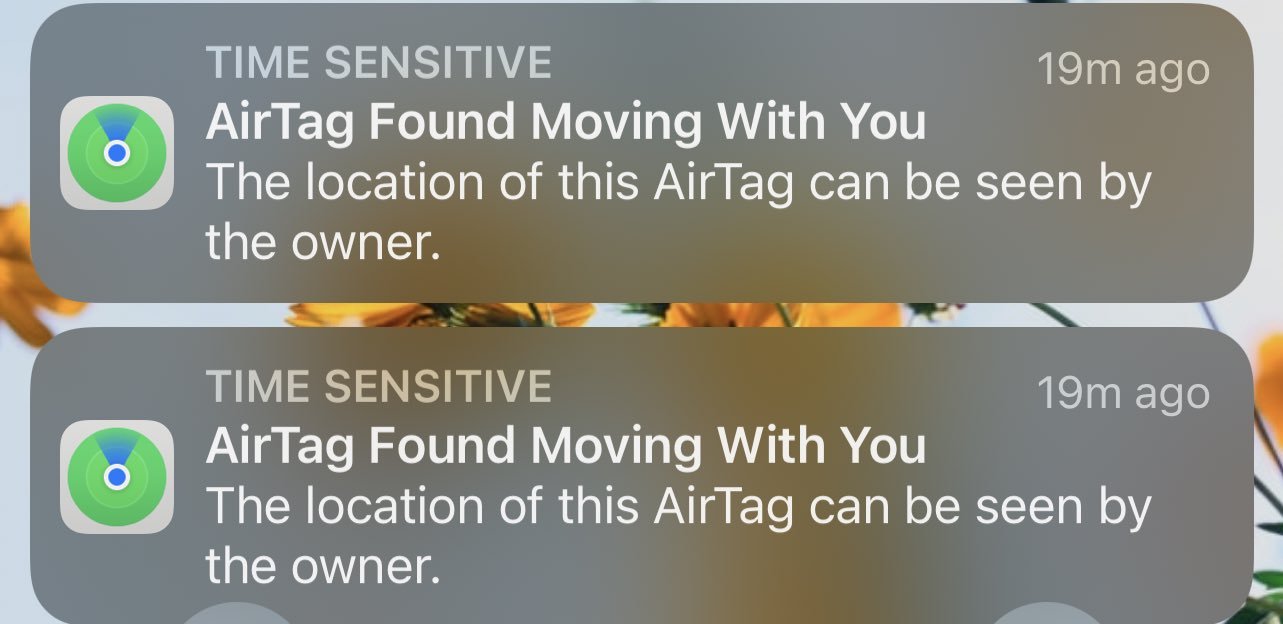
The AirTag Conundrum: Apple Needs to Fix This!
AirTags are being used to stalk folks, and it needs to be fixed!
Is it Time to Let Go of Your RMM?
This question is quickly becoming the hottest question in the channel, especially after the Kaseya incident. In this article, I’ll illustrate a kill chain with an RMM-based attack, some thoughts on attack surface reduction, and some thoughts on ditching the RMM altogether.
Protect Yourself from BECs by Empowering Your Team
It's cliché by now:Your users are your best cyber defenders.I hear that and sometimes I feel it's getting old, but it's so very true. In this article, let's take a look at Business Email Compromises (BECs), and how we can empower our people to protect the business...
Knocked out my first LinkedIn Live stream!
Live streaming is always something I’ve wanting to dabble in. I’m a terrible gamer. Like, the worst. But I’m a pretty good talker when it’s a subject I’m comfortable with. I’m an even better talker when I can surround myself with smart friends!What’s where I came to...