Raw Thoughts
Stop Using Magic Links
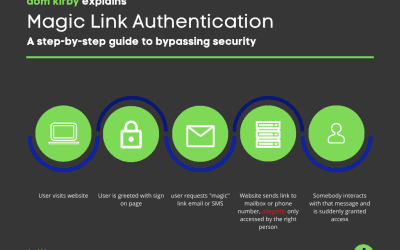
Click here to get a link to login. Magic links are suddenly everywhere, and I simply refuse to accept the logic behind them. Before I rant a bit about why you shouldn't be using them, let's talk through the basic concept behind it: At a high level, magic link...
Imposter Syndrome is a Sign of Progress!
We've all been there; in fact I feel like I'm there all the time. Imposter syndrome is real, in almost every industry. As we move up in our careers, tackle new challenges, or start to educate others, it sets in. We start to feel inadequate in our own world. It can be...
Will there be a cyber war?
As a cyber nerd, my first question when tensions went up in the region was 'what are the cyber implications?' The atrocities happening in Europe are shocking for everyone, and this is certain to be in history books in the same way 1939 is. However, it's different. I'm...
No More Third-Party MFA for Delegated Admin
In a subtle update to the Microsoft Partner Security Requirements article on February 24th, Microsoft precludes the use of third-party MFA for partners wanting to take advantage for Delegated Admin Privileges (DAP) or Granular Delegated Admin Privileges (GDAP). They...
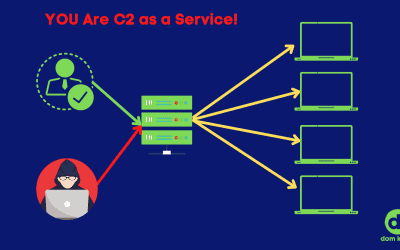
It’s Time: Drop Persistent Remote Access
Threat actors are using your infrastructure for command and control as a service! When it first became a thing, remote controlling a computer was a thing of magic. So much "how are you doing this?!" Threat actors have caught onto this. Creating one convenient place to...
Modern Security Baby Step: Safe Links and Safe Attachments
In my previous Baby Steps episode, we reviewed smart ways to implement data loss protection for every client. This episode focuses more so on outward protection with Safe Links and Safe Attachments in Defender for Office 365. This is available as a part of the...
Speaking of Digital Transformation: I Lost my Wallet
My kids disappeared my wallet into the Twilight Zone that only kids have access to. We've turned the house upside down looking for it. If you're a parent, you either know what I'm talking about, or you will someday. It's a pain, but not as much of a pain as I thought....
Modern Security Baby Step: Data Loss Prevention
After my previous Modern Security Baby Step, I posted a poll on LinkedIn so that you could decide the next topic! Surprisingly, you voted on Data Loss Prevention Rules I recommend for all! So, let's talk about DLP! Data Loss Prevention is a simple concept. Hunt the...
Text Messaging is Bad MFA
Ahh texting. Arguably the start of the digital communications revolution. The good ‘ol short message service (SMS). To this day, texting is a key method of communication. However, there’s one key thing that texting is not: secure.