Raw Thoughts
How is your MSP’s content game?
Content, and marketing in the MSP space in general, is totally broken. But you can fix it in your own practice!
Modern Security Baby Steps: Mobile Application Management
Implementing MAM is one simple step that you can take for a quick security gain! It will help ensure that data on untrusted devices is at least controlled and protected.
MFA is a Compulsory Item
I might generate a bit of a stir, but this must be said! You cannot be defensible if you are not meaningfully implementing multi-factor authentication. If I'm being honest, having this conversation is getting so old. We've been having it for years yet, somehow,...
Microsoft’s Cyber Signals: Identity is the New Battleground
Microsoft is one of the most powerful, intelligent cybersecurity firms on the planet. Many people don't realize just how much intelligence Microsoft has at their disposal. In their new intelligence brief series, Cyber Signals, Microsoft is pulling back the curtain and...
2022 Prediction: Digital Transformation will Drive Talent Acquisition
Technology serves business, not the other way around. Technology and the services around it aren't (or shouldn't be) commodities. For too long, we've been commoditizing our capabilities and selling widgets. Help desk service, servers, this and that as a service, what...
How I’d Approach NCE
Microsoft’s New Commerce Experience comes with substantial changes to the way we’re used to doing business with Microsoft. From price increases to extra price increases for monthly terms, it can really complicate your business model as an MSP. In this article, I’ll touch on how I would approach NCE and what changes I would have made to my model.
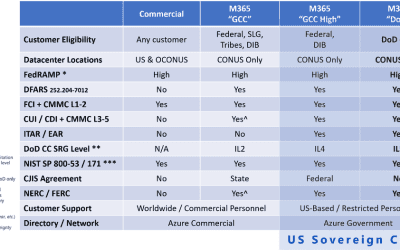
Where do I put my data? The Layers of Microsoft Cloud
Knowing where to store your data, specifically gov data, based on its type can be tricky. Microsoft has helped peel back the veil.
Review: FEITIAN Security Keys
FEITIAN recently reached out to me on LinkedIn and asked if I’d be willing to take a look at their security keys. As you may know, I’m a major proponent of FIDO/U2F, and I’ve been a Yubikey user since it was just YOTP. That said, I was curious to check out FEITIAN’s...
No Framework Can Mean No Defensibility
Frameworks are extremely important in the modern security landscape. With the level of complexity of today’s average environment, even in the SMB arena, shooting from the hip is hardly an option anymore. In fact, I’d almost challenge that the way the SMB sector has approached security for well over a decade has just been plain wrong, let’s dive in.